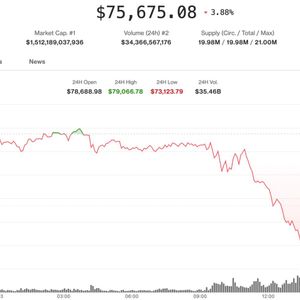
BitcoinWorld CrossCurve Exploit: Devastating $3M Cross-Chain Bridge Hack Exposes DeFi’s Fragile Security In a stark reminder of the persistent security challenges facing decentralized finance, the CrossCurve protocol has suffered a devastating exploit, resulting in the suspected theft of approximately $3 million. This major security breach, first reported by Cointelegraph citing data from security firm Defimon Alerts, targeted the protocol’s cross-chain bridge infrastructure. Consequently, the incident has triggered immediate protocol shutdowns and renewed urgent discussions about validator security and smart contract audits within the DeFi ecosystem. CrossCurve Exploit: Anatomy of a $3 Million Attack The CrossCurve exploit represents a sophisticated attack vector within the rapidly evolving cross-chain landscape. According to the initial investigation, the attacker successfully bypassed critical validator procedures embedded within a specific smart contract. This clever bypass allowed the malicious actor to send forged cross-chain messages. These fraudulent messages then triggered the unauthorized unlocking of tokens held within the bridge’s custody. Security analysts quickly identified the attack’s signature across several blockchain networks, confirming the multi-chain nature of the theft. The protocol’s team confirmed the breach via a post on X, explicitly stating a smart contract vulnerability had been exploited. They urgently advised all users to halt interactions with the protocol pending a comprehensive investigation. Understanding the Cross-Chain Bridge Vulnerability Cross-chain bridges serve as essential infrastructure, enabling asset transfer between different blockchain networks. However, they also present concentrated points of failure. The CrossCurve incident highlights a critical weakness: the security of the message validation mechanism. In a typical bridge, validators or oracles verify the legitimacy of a transaction on one chain before authorizing a corresponding action on another. The attacker in this case found a flaw to circumvent this verification process entirely. This breach methodology shares similarities with previous high-profile bridge hacks, including the Wormhole and Ronin Bridge exploits, which collectively resulted in losses exceeding $1 billion. The table below contrasts key aspects of recent major bridge exploits: Protocol Year Estimated Loss Primary Attack Vector Ronin Bridge 2022 $625 million Compromised validator keys Wormhole 2022 $326 million Signature verification flaw Nomad Bridge 2022 $190 million Upgrade initialization error CrossCurve Bridge 2025 $3 million Validator bypass & forged messages This pattern underscores a systemic issue. While the financial scale of the CrossCurve hack is smaller, the technical premise remains alarmingly consistent. Bridges aggregate immense value but often rely on complex, novel code that undergoes less battle-testing than core blockchain layers. The Michael Egorov Connection and Protocol Backing The CrossCurve protocol had garnered significant attention due to its backing by Michael Egorov, the founder of the leading decentralized exchange Curve Finance. Egorov’s association provided a layer of credibility and technical expectation. Curve Finance itself is a cornerstone of the DeFi ecosystem, specializing in stablecoin trading with billions in total value locked. This backing makes the exploit particularly noteworthy, suggesting that even protocols with esteemed technical advisors remain vulnerable to sophisticated attacks. The incident may prompt a re-evaluation of how founder endorsements influence perceived security versus actual protocol robustness. It demonstrates that security is a function of relentless auditing and formal verification, not just pedigree. Immediate Impact and Broader DeFi Repercussions The immediate impact of the CrossCurve exploit is multifaceted. First, users face direct financial loss and must wait for the investigation to determine any possibility of recovery. Second, the protocol is effectively frozen, disrupting its functionality and any projects or users relying on its cross-chain services. More broadly, this event contributes to a concerning trend. According to annual reports from blockchain security firms like CertiK and Chainalysis, cross-chain bridge hacks have constituted a dominant share of total crypto theft in recent years. This recurrence erodes user trust and potentially slows institutional adoption of cross-chain solutions. Furthermore, it places increased regulatory scrutiny on the DeFi sector, as lawmakers point to these incidents as evidence of consumer protection gaps. The market often reacts negatively to such news, creating sell-side pressure on related assets and sectors. Security Lessons and the Path Forward for Bridge Design The CrossCurve bridge hack offers several critical lessons for developers and the wider DeFi community. Primarily, it reinforces the need for extreme rigor in designing validator and oracle systems. Potential mitigation strategies gaining traction include: Multi-layered validation: Implementing multiple, independent validator sets with diverse software clients. Time-delays and withdrawal limits: Introducing mandatory waiting periods or caps on large transfers to allow for threat detection. Enhanced monitoring: Employing real-time transaction analysis tools to flag anomalous cross-chain message patterns. Decentralized fault proofs: Using systems where anyone can challenge invalid state transitions, creating a community-powered security layer. Ultimately, the industry may need to shift towards more minimalist and formally verified bridge designs. The pursuit of maximum capital efficiency and speed must be balanced against fundamental security guarantees. This exploit will likely accelerate research into zero-knowledge proof-based bridges and other trust-minimized architectures. Conclusion The CrossCurve exploit, resulting in a suspected $3 million loss, is a significant event that highlights the ongoing vulnerability of cross-chain bridges in DeFi. This attack, involving the bypass of validator procedures to forge cross-chain messages, echoes the root causes of historically larger breaches. While the immediate financial damage is contained relative to past hacks, the technical implications are profound. It underscores that security in this innovative space requires continuous, adversarial testing and defense-in-depth principles that go beyond reputable backing. The CrossCurve incident serves as another crucial data point, pushing the industry toward more resilient, transparent, and robust cross-chain communication protocols. The path forward depends on learning from these failures and prioritizing security over sheer functionality. FAQs Q1: What exactly was stolen in the CrossCurve exploit? The attacker stole approximately $3 million worth of various cryptocurrencies that were locked within the protocol’s cross-chain bridge, across several supported blockchain networks. Q2: How did the hacker manage to bypass the bridge’s security? The exploit involved bypassing the bridge’s validator procedures. The attacker found a vulnerability in a specific smart contract that allowed them to send forged cross-chain messages, which then tricked the system into unlocking tokens without proper authorization. Q3: Is there any chance users will recover their lost funds? While recovery is never guaranteed, the protocol team is investigating. Options may include negotiating with the attacker, pursuing legal avenues, or using a treasury fund if one exists. However, users should prepare for the possibility of permanent loss, as is common in DeFi exploits. Q4: What does Michael Egorov’s involvement with CrossCurve mean for this incident? Michael Egorov, founder of Curve Finance, was a supporter of the CrossCurve protocol. His involvement lent credibility but did not immunize the protocol from vulnerabilities. This shows that security is separate from technical pedigree and must be validated through independent audits and robust design. Q5: Are all cross-chain bridges unsafe to use now? Not all bridges are equally vulnerable, but the CrossCurve exploit is a reminder that they are complex and high-value targets. Users should exercise caution, research a bridge’s security audits, its track record, and the design of its validation mechanism before depositing significant funds. Diversifying assets across different bridges can also mitigate risk. This post CrossCurve Exploit: Devastating $3M Cross-Chain Bridge Hack Exposes DeFi’s Fragile Security first appeared on BitcoinWorld .